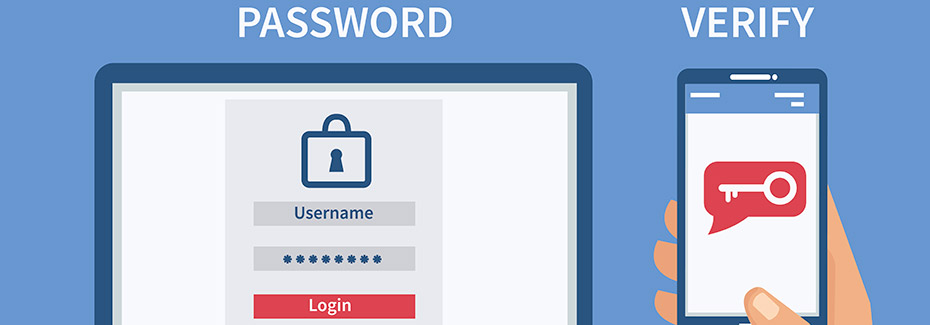
Here’s an example of what multi-factor authentication (MFA) is not. For instance, you head to your online bank account to login. Entering the username and password into the designated fields and click on login. From here, you’ve gained access to your bank information. Easy peasy and you go about your business. Wait one second! If you’re one of the 54% of consumers who use five or fewer passwords for all of your online accounts, you could be setting yourself up for failure.
Recycling passwords is a big no-no. We highly advise coming up with unique passwords for all digital channels. We published a blog post discussing the importance of unique passwords and why using the same password is bad.
Let’s dive right in and discuss the benefits of multi-factor authentication.